October 2020 - In this interview, Colin Blanchard of BT discusses the topic of IoT security.
Q: Let us begin by talking about your background and roles in BT and oneM2M.
CB: I began working as a Security Consultant in BT in 1995 and soon became involved in analysing the security of new products and services, especially those related to mobile and IoT offers. Over time, I took a wider view of security and privacy in the context of standardisation bodies. I now have responsibility for Security Standards strategy via BT’s Security and Cyber Defence roadmap. My main objective is to ensure that we have and use international standards in our products and services, while avoiding overlap and duplications in the various standards development organisations (SDO) and industry bodies.
I became involved in IoT security standardisation around 2008 when smart utility meters drew a lot of industry attention. At the time, there was a lot of debate about security and privacy issues. Some of the early thinking began in 3GPP and dealt with Subscriber Privacy Impact (SPI) issues for machine-type communications (MTC). This initiative was eventually transitioned into oneM2M standardisation activities.
Q: Why has the oneM2M initiative become important for the IoT industry?
CB: In the case of the connected home, it is important to provide integrated services. We have seen interest in this approach from a variety of sectors such as utilities, building management companies, transportation agencies, the automotive industry, insurance companies and local authorities, among others. Each of these sectors is making greater use of IoT technologies and services. As a provider of telecommunications services, we see demand for assistance in managing IoT services for our customers.
IoT technologies also open up new opportunities. Take the example of a business that manages a remote, industrial asset as part of its day-to-day operations. The data and usage profile of that asset might be valuable in getting a better insurance rate. IoT now creates a new business opportunity for the insurance sector. For IoT to become as pervasive as mobile communications, there is a need for a standardisation framework to handle a wide variety of IoT use cases and to do so globally. That is what oneM2M provides and why it is important for the IoT industry.
Q: IoT security is a large topic so how would you define its scope?
CB: I believe that it is important to work back from three key issues. The first is the proliferation of connection standards, device operating systems and, use cases. Security has to work across a large number of permutations, so the industry needs a standardized and systems-based approach.
The second issue is that we are not working as if we are surrounded by smartphone-like devices. Designers must work on the basis that many IoT devices and applications will exist in the background, as unattended applications. We cannot count on there being human users to “feed and water them”. That involves designing security from the outset and automating many security functions.
Finally, IoT devices generally operate with long service lifecycles which have to be factored into the business case for access and physical replacement. However, user expectations and applications move as fast as the consumer market. Security needs to bridge these timing differences. This brings life-cycle management issues into play and the need for cost-efficient security management tools which are more likely to come from a standards-based approach.
Q: How is oneM2M tackling the issue of IoT security?
CB: oneM2M started to look at new requirements for IoT security from an early stage, well before the market caught on to the importance of these issues. In 2008, for example, BT and several other companies initiated some of the early work on remote provisioning for machine type devices – those not requiring the presence of a human user. That work was done within 3GPP SA3 and reported in TR33.812, a “Feasibility study on the security aspects of remote provisioning and change of subscription for Machine to Machine (M2M) equipment”. oneM2M took the ideas from this exercise into normative specification work, specifically for certificate-based credentials. These specifications are a fundamental part of the GSMA’s eSIM specifications and provide the solutions to address SIM-based credential requirements.
Looking at matters from a broader context there are many facets to IoT security which oneM2M tackles in a logical sequence through its standardisation roadmap. oneM2M Release 1 provided basic security features in the form of a common service function (CSF) that any IoT device or application entity can call upon. The capabilities within this security CSF ensure that only legitimate applications can access resources, but also that applications can confirm that the requested resources are legitimate (i.e. Mutual Authentication). Also included were pre-provisioned features (i.e. Access Control Lists) to restrict access based on specific criteria, such as an authenticated identity, location, and time of day among others (i.e. Authorisation).
The design of cellular IoT systems ensures the confidentiality and protects the integrity of communications involving set-up and content messages. However, these protections are terminated and re-enabled at each node in the communication path (hop by hop). An end-to-end security framework requires all these nodes to be trusted so that they do not modify or leak the information being relayed. As deployments grow in size and complexity, however, it becomes impossible to predict what access will be required and who and what to trust. For this reason, Release 2 added features to dynamically add and withdraw authorisation using tokens. Release 2 also added end to end encrypted set-up messages and message content, so that intermediate nodes in the path do not need to be trusted.
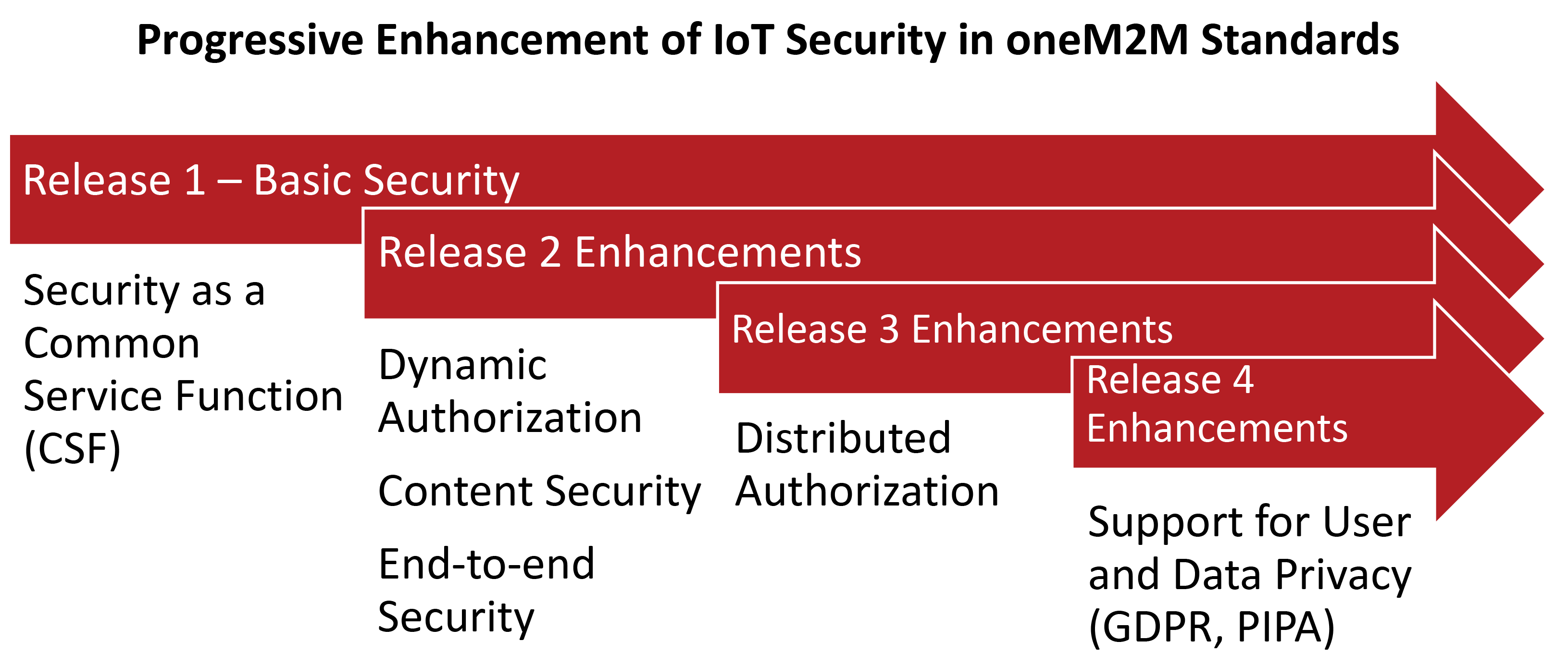
While the focus of oneM2M is on machine and IoT communication without the involvement of any human users, it is of course for their ultimate benefit. Releases 3 and 4 add features for identifying and authorising such users, but at the same time including features to protect their privacy as required by local regulations, such as GDPR (Europe) and PIPA (Korea).
As you can see, there has been a lot of work done within oneM2M on IoT security and privacy. I would like to take the opportunity to draw your readers’ attention to several on-going activities and publication resources. We are currently working on a security section of a “Getting started with oneM2M” technical report. This introduces security to a non-technical audience and describes how oneM2M specifications address the three issues I described earlier. There is also a work item on the registration of privacy profiles. This is a preference profile for end users which defines what data an IoT service collects and shares with IoT vendors.
I spoke about avoiding overlap and duplications in SDOs earlier so a part of what oneM2M does is to liaise with other bodies. We maintain a dialogue and reference work done on device security by the GSMA and ETSI’s Technical Committee on CyberSecurity (TC Cyber). In the international arena, some national governments mandate ITU-T documents in procurements and in licenses to operate services. We are close to completing the work to transpose oneM2M’s security specification TS-0003 into an ITU-T SG20 Y series which provides specifications for M2M Security and Privacy protection.
Q: Finally, what advice would you offer to developers and users of IoT technology on the topic of security?
CB: Developers and service providers have a duty of care to consumers and to operators providing the connectivity even though they may think their service, such as an automatic dog bowl feeder, is not a part of the critical national infrastructure or does not have a privacy impact on their customers. There is plenty of help available from oneM2M, ETSI TC Cyber, the GSMA and the IoT Security Foundation.
