December 2025 - In 2024, oneM2M interviewed Luigi Liquori (LL) to learn about his work in developing an asynchronous contact tracing (ACT) protocol as an upgrade to the early protocols deployed during the COVID pandemic. ACT allows individuals to find out if they might be at risk from residual virus deposited by an infected person who had passed through that a given location some time earlier. ACT has advantages over synchronous tracing approaches because the latter deals with situations where two people are in the same, 2-meter vicinity at the same time. As outlined in a Nature publication, this narrows the scope effective contact tracing. Data from the UK, for example, revealed 3% to 5% success rates.
 To learn about how the ACT approach is being extended, we hear from Egan Perais (EP). He recently completed a student internship with Luigi Liquori, INRIA Senior Research Scientist. The first stage of Egan’s project was to extend cloud implementation of the ACT application. Subsequently, he began work on applying the ACT concept to drone and distributed IoT device situations. Some of which are relevant to military defence situations. Joining Egan in this interview are Luigi Liquori and Andreas Kraft (AK), whose ACME CSE forms the basis of implementation experiments.
To learn about how the ACT approach is being extended, we hear from Egan Perais (EP). He recently completed a student internship with Luigi Liquori, INRIA Senior Research Scientist. The first stage of Egan’s project was to extend cloud implementation of the ACT application. Subsequently, he began work on applying the ACT concept to drone and distributed IoT device situations. Some of which are relevant to military defence situations. Joining Egan in this interview are Luigi Liquori and Andreas Kraft (AK), whose ACME CSE forms the basis of implementation experiments.
Q: Would each of you begin by introducing yourselves to our readers?
EP: I completed my studies in general engineering at ESIGELEC in Rouen (France), where I mainly studied cybersecurity and IoT. I completed a four-month internship at the Inria Center at Université Côte d'Azur, where I worked with Dr. Liquori. I am currently doing a second four-month internship following on from the first, but this time at the Social, Mobile, Data & Crowd (SMDC) Laboratory at University of Udine in Italy, under the guidance of Professor Ivan Scagnetto. I am due to graduate in April 2026.
LL: I am a former theoretical computer scientist who switched to telecom and then to academic research. I worked at the Centro Studi e Laboratori Telecomunicazioni (CSELT) of Telecom Italia and the École Normale Supérieure of Lyon. I then went on to become a Lecturer at the Ecole Nationale Supérieure des Mines of Nancy. In 2001, I moved to INRIA, the French National Institute for Research in Computer Science and Technology. My research focuses on the semantics and logics of computation, semantics of programming languages and IoT protocol standardization. I also have a strong interest in protocols for overlay networks, in particular Peer-to-Peer protocols and Content-based Networks, when applied to IoT, and especially to oneM2M, Smart Contracts, and Blockchain. I am currently working with ETSI’s TC DATA committee and a group in the International Standards Organization (ISO) at the intersection of finance, law, and computer sciences to develop smart, legal contracts.
AK: I used to work for Deutsche Telekom (DT) as a principal enterprise architect, focusing on standardization and innovation management. I was involved in the Internet of Things (IoT) for many years. I now work as a consultant for oneM2M technologies. My focus is on the development of oneM2M’s technical specifications and the promotion of oneM2M standards in the IoT ecosystem. I am also the author and maintainer of the ACME CSE open-source project, which implements a oneM2M-compliant Common Services Entity (CSE).
Q: How are the ACT principles and application being extended?
LL: My early focus was on tracking “Venn-diagram” intersections between people and their smartphones during the COVID pandemic. The basic tracking principles apply to any moving device or sensor. One example is to look at drone patrols as part of the broader topic of interconnecting, mobile IoT. In fact, ETSI launched an 18-month project under a Specialist Task Force (STF 697) in July 2025 on the topic of pathogen detection systems (PANDESYS).
EP: For my internship between May and August of this year (2025), I investigated a cloud-based implementation of ETSI TS 103 757, Asynchronous Contact Tracing (ACT) using oneM2M. This employed a large scale ACME CSE, which is probably the most complete oneM2M implementation. The project is a stepping stone to developing zonal systems managed by different system operators or agencies which would allow one region to collaborate with another by sharing data. Imagine tracking a roving IoT device in one zone and then sharing information about its movements with the owner of a neighbouring zone. After this INRIA internship, I moved into a project at the SMDC Lab, University of Udine in Italy that deals with theoretical and practical aspects of Mobile, Pervasive, and Ubiquitous Computing, where I’m working with the Professor Scagnetto. I should add that everything involves oneM2M standards which are new to me.
AK: Another interesting use case that builds on the ACT concept will come out of the ESTIMED project. ESTIMED is a tie-up between ETSI’s Multi-Access Edge Computing activities and oneM2M. The use case deals with smarm computing where many mobile devices collaborate in small groups as part of a wider system.
Q: What has been your experience in learning about and applying oneM2M standards?
EP: Well, the standard is quite large, so my early days involved a lot of learning both about oneM2M and ACT. There is a definite method to reading standards documents. I was already familiar with the ISO’s cybersecurity standards from my academic studies. That experience helped me to read and understand oneM2M documents.
One of the things that helped me in my learning journey was the ACME CSE. I also received a lot of guidance from people like Bob Flynn (oneM2M’s TDE Chair) and Andreas Kraft.
AK: I would like to add that aside from the ACME CSE, people who are learning about oneM2M also find the ‘Recipes’ especially useful. These are small, solution examples with code snippets that act as implementation references.
Q: Would you describe the application you built?
EP: Since my project aims were to make progress on deployment topics and to evaluate technical-stack performance, I built a proof of concept using ACME CSE. There are other oneM2M stacks, such as tinyIoT which is a lightweight, C-based oneM2M CSE that could be targeted.
AK: The availability of oneM2M technical stacks is an important point. Since we are interested in standardization, the idea is to allow developers to interchange stacks. That is one of the benefits of standardization, after all.
LL: As the project progresses, there will be opportunities to evaluate the switchover between ACME CSE and tinyIoT at "large scale" using the INRIA cloud.
EP: After deploying an ACME CSE instance on INRIA’s cloud infrastructure, I then built a graphical control panel to manage deployed sensors. This allows a system manager to create sensors or oneM2M application entities and place them geographically on a map.
For the purposes of this project, we are working with simulated sensors. However, the current implementation can mix real sensors, making the full ACT picture very intriguing and useful. The configuration of these sensors simulates time series readings for environmental data such as temperature or air-borne particulates, pollution of any "hostile" event, for example. There are system settings that allow us to filter data through configurable alert or alarm threshold settings. It is also possible to configure these sensors with image processing capabilities to enable image recognition triggers.
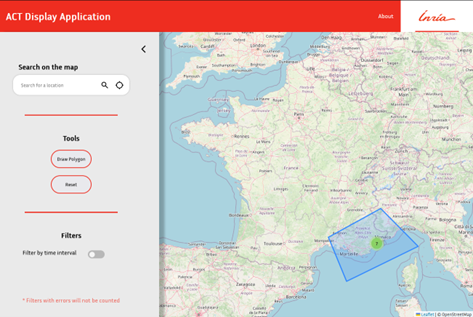
LL: With a large population of deployed sensors, a user can click and connect pointers to designate an enclosed geographical area on the map to see which devices fall inside its footprint. By footprint here we mean that the ACT standard takes advantage of a mobile phone application, running in background, that registers the passage of the smartphone owner, i.e., there is a digital footprint of the places a person visited. The user can later to select a given geographical area for the purpose of seeing which sensors have detected a virus so far. There are many possible applications of ACT, ranging from eHealth to Smart Cities. Embedding drones with the mobile application add another kind of useful applications, ranging from security, patrolling applications, to underwater archaeology as Professor Scagnetto is demonstrating through his work.
EA: Here are a few screen shots from the ACT console to illustrate the process I outlined. To begin with, here is the console that greets users. The map centers on France for this illustration.
Next, the user designates an area of interest
On zooming into the designated area, the console displays what sensors are present. Clicking on the sensor symbol presents the user with each sensors’ information.
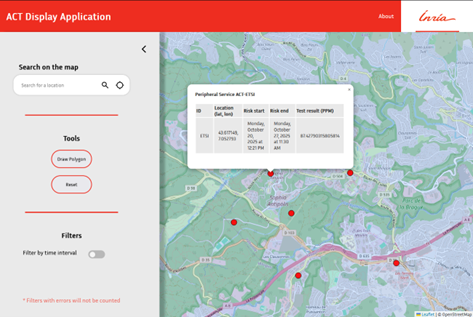
The user can also specify a time interval to search back in time and see whether a user or a drone might have visited that area in the past. A future enhancement is to perform forecasting at user-specified intervals in the future. This will require to use classical LLM-based AI algorithms.
Q: What other initiatives are planned, to build on the proof of concept?
EP: At the moment, the design focuses on having one system manager. We need to think in terms of a distributed system, comprising multiple CSEs, where there might be several managers and their applications. ACT aims to ensure communication between all CSEs under the common communication umbrella of oneM2M. It makes sense for each application to work with others. That results in a mesh system, which raises several research questions about complexity, scale, and performance.
LL: Egan and his colleagues implemented this ACT prototype and installed it on the INRIA cloud which is one of the largest cloud academic infrastructures in France. Imagine we built a system of distributed ACME CSEs, each able to communicate and collaborate with one another. This is what we are developing using container techniques (Docker). The aim is to make a publicly accessible dashboard with multiple ACME CSE instances on INRIA’s cloud infrastructure and then to experiment with large-scale cooperative or federated IoT systems.
In the new applications of ACT with drones, another interesting topic for investigation is to solve the challenge of a managing a drone that travels between two zones. There needs to be a procedure for the drone to de-register from one CSE and re-register to the second one. This will require to use an underlay peer-to-peer protocol that will eventually make its way into the standardization roadmap.
AK: We are seeing such considerations come up in the ESTIMED project with questions about what kind of orchestration model might be required. These solutions will build on the security and access- or permission-control capabilities in oneM2M. Something else to think about is the topic of semantic routing, which is a new frontier for research.
Q: What lessons are you learning about implementation challenges?
EP: I am still learning a lot about cloud computing and the use of Docker technology as I move from a local host model to a cloud solution. System administration and scaling strike me as the biggest challenges. That is because the IoT label encompasses a melting pot of standards and technologies.
AK: As a more experienced developer, I can see Egan’s learning journey progressing. I think that DevOps for IoT systems are a lot different from the procedures one would follow when deploying an enterprise accounting application, for example.
As we look at scaling up systems with many IoT sensors, there is also the issue of transactional loads on communications networks. Many devices sending lots of small payload messages can be completely overwhelming for networks built around people and smartphone streaming. Again, from our early work in the ESTIMED project we can see the value of moving computing closer to the edge, beginning with mobile network base stations. This is analogous to existing content distribution networks (CDNs) that place streaming content closer to users. We are on the threshold of IoT 2.0 which will feature a lot of interconnected networks and compute devices.
Q: Where can readers get more information on the topics you have shared with us?
EP: Once the documentation is completed, it will be available on the public ACT Inria: https://gitlab.inria.fr/act and https://act.gitlabpages.inria.fr/website/
